A safeguard or countermeasure prescribed for an information system, or an organization designed to protect the confidentiality, integrity, and availability of its information and to meet a set of defined security requirements.
- NIST Definition of Security Control
Security Controls, the topic of this post, represents the natural intersection between compliance and cybersecurity. For example, they are one of the best ways to demonstrate the “Accountability” requested by GDPR in many articles to data controllers and data processors.
This content may be helpful for you if you are cybersec or privacy practitioner or if you are studying for a Cybersec Certification like CISSP, CISM, CRISC, CEH, ….
It is a theoretical subject; therefore, you might find it abstract and dry to grasp. Nevertheless, it is fundamental to be able to talk the official lingo of cybersecurity and is very frequently tested in cybersec exams.
This content is provided chewing and digesting the information collected from the following sources:
1. “All In One CISSP Exam Guide 9th Edition” by F. Maymì and S. Harris
2. “Official (ISC)2 Guide to the CISSP CBK”, Sixth Edition by A. Deane and A. Kraus
3. “Sybex CISSP Official Study Guide 9th Edition”, by M. Chapple, JM Stewart, D. Gibson
4. “The effective CISSP – Security and Risk Management” by Wentz Wu
Please be informed that the information provided in this tutorial is for informational and educational purposes only. Any reliance you place on this information is at your own risk.
Security controls are designed to reduce the likelihood that a vulnerability will be exploited by a threat. By implementing security controls, organizations can mitigate the risk of vulnerabilities being exploited and protect their assets from harm.
The aim of security control, as stated by NIST, is to preserve Confidentiality , Integrity and Availability of information. The term control is interchangeable with the following terms: countermeasure, safeguard, security mechanism, protection mechanism. But it is possible that ISACA in its exams distinguishes countermeasures (related to the process) from controls (related to the means).
In this table we can see a common classification of Security Controls. There are infinite possible classifications, what we’ll see is just the most common classification in the infosec field.
This content may be helpful for you if you are cybersec or privacy practitioner or if you are studying for a Cybersec Certification like CISSP, CISM, CRISC, CEH, ….
It is a theoretical subject; therefore, you might find it abstract and dry to grasp. Nevertheless, it is fundamental to be able to talk the official lingo of cybersecurity and is very frequently tested in cybersec exams.
This content is provided chewing and digesting the information collected from the following sources:
1. “All In One CISSP Exam Guide 9th Edition” by F. Maymì and S. Harris
2. “Official (ISC)2 Guide to the CISSP CBK”, Sixth Edition by A. Deane and A. Kraus
3. “Sybex CISSP Official Study Guide 9th Edition”, by M. Chapple, JM Stewart, D. Gibson
4. “The effective CISSP – Security and Risk Management” by Wentz Wu
Please be informed that the information provided in this tutorial is for informational and educational purposes only. Any reliance you place on this information is at your own risk.
Security controls are designed to reduce the likelihood that a vulnerability will be exploited by a threat. By implementing security controls, organizations can mitigate the risk of vulnerabilities being exploited and protect their assets from harm.
The aim of security control, as stated by NIST, is to preserve Confidentiality , Integrity and Availability of information. The term control is interchangeable with the following terms: countermeasure, safeguard, security mechanism, protection mechanism. But it is possible that ISACA in its exams distinguishes countermeasures (related to the process) from controls (related to the means).
In this table we can see a common classification of Security Controls. There are infinite possible classifications, what we’ll see is just the most common classification in the infosec field.
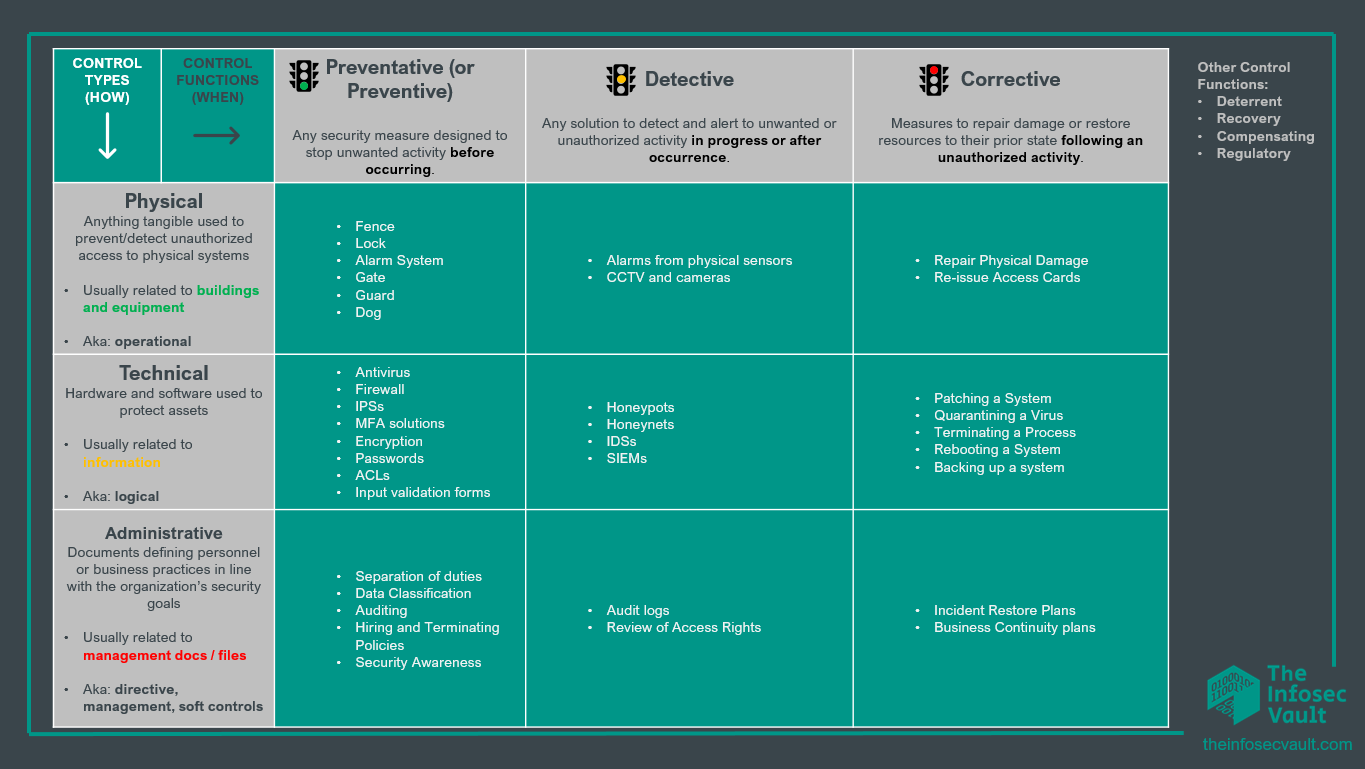
The taxonomy of security controls will depend on the specific needs and goals of an organization, as well as the types of risks and vulnerabilities it is facing, for example:
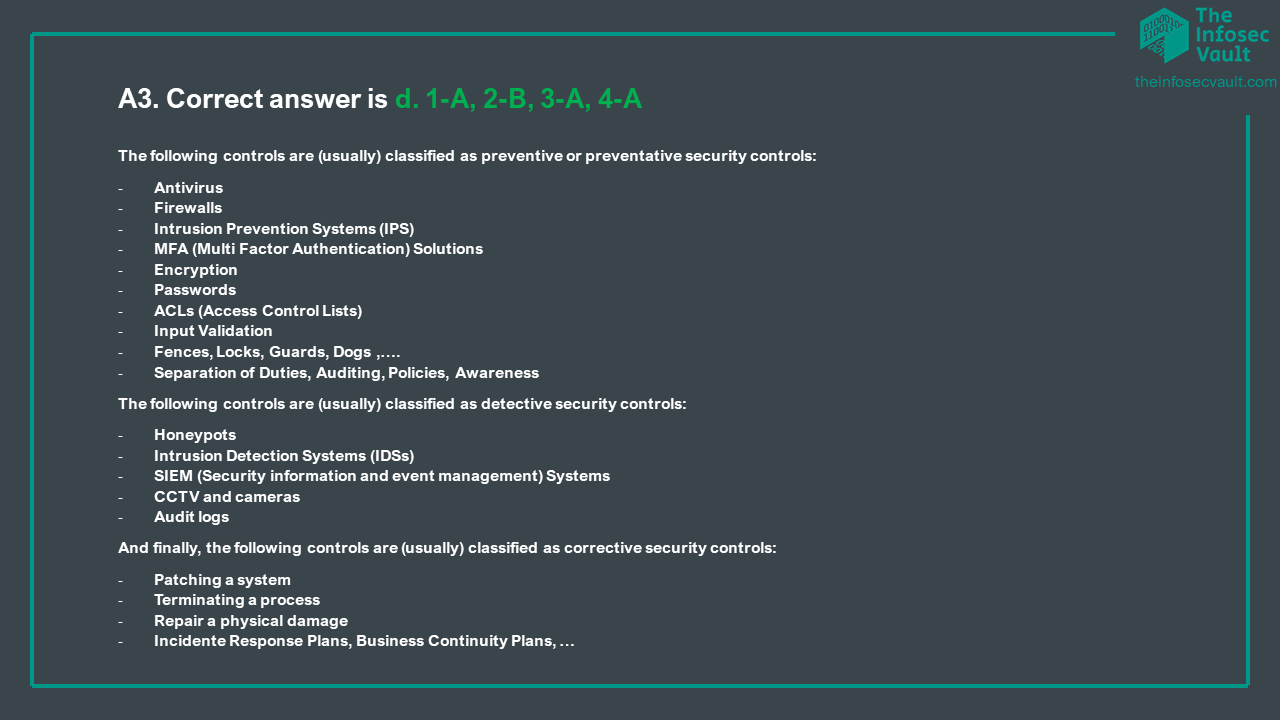
- ISO 27001:2022 has 4 control categories and 93 controls
- ISC2 CISSP CBK has 7 types NIST SP 800-53 has 18 families
By the way, usually, Security controls are classified in 2 different ways: security control types and security control functions, and this classification should be enough for your infosec certification or interview.
Control types, reported in the y axis of the table, usually answer the question “how are we protecting our assets” and are divided in:
Physical Controls are tangible measure used to protect (or detect) unauthorized access to physical systems or areas.
Technical Controls include the measures implemented through technology, such as software, hardware, or network systems to protect assets.
Administrative Controls are measures (usually documents) implemented through policies, procedures, and other organizational measures defining personnel or business practices in line with the organization security goals.
The second way of classifying security controls is by Control functions, depicted in the x axis of the table, which are preventative, detective, and corrective. Despite their name, they usually are related at the time in which an incident happened, more specifically security control functions help us in classifying countermeasures happening before, during and after an incident or an unauthorized activity. Let’s shortly describe them.
Preventative controls comprehend any security measure designed to stop any unwanted activity from occurring.
Detective Controls are the solutions to detect and alert to unwanted or unauthorized activity in progress after occurrence.
Corrective Controls are the measures to repair damage or restore resources to their prior state following an unauthorized activity.
We put in the table some controls, if you’re working in the IT field some of them, like for example dogs, could sound fancy, but always remember that anything used to mitigate a risk is a security control, and what you see in the table is just a possible classification.
As we previously said there isn’t a standard classification nor taxonomy for security controls, for example to make things a bit more complicated (but do not worrie they are not too complicated) (ISC)2 classifies controls in 7 types based on the timing of unauthorized behaviors by motive, opportunity and means (MOM). You find them in this table:
- ISO 27001:2022 has 4 control categories and 93 controls
- ISC2 CISSP CBK has 7 types NIST SP 800-53 has 18 families
By the way, usually, Security controls are classified in 2 different ways: security control types and security control functions, and this classification should be enough for your infosec certification or interview.
Control types, reported in the y axis of the table, usually answer the question “how are we protecting our assets” and are divided in:
Physical Controls are tangible measure used to protect (or detect) unauthorized access to physical systems or areas.
Technical Controls include the measures implemented through technology, such as software, hardware, or network systems to protect assets.
Administrative Controls are measures (usually documents) implemented through policies, procedures, and other organizational measures defining personnel or business practices in line with the organization security goals.
The second way of classifying security controls is by Control functions, depicted in the x axis of the table, which are preventative, detective, and corrective. Despite their name, they usually are related at the time in which an incident happened, more specifically security control functions help us in classifying countermeasures happening before, during and after an incident or an unauthorized activity. Let’s shortly describe them.
Preventative controls comprehend any security measure designed to stop any unwanted activity from occurring.
Detective Controls are the solutions to detect and alert to unwanted or unauthorized activity in progress after occurrence.
Corrective Controls are the measures to repair damage or restore resources to their prior state following an unauthorized activity.
We put in the table some controls, if you’re working in the IT field some of them, like for example dogs, could sound fancy, but always remember that anything used to mitigate a risk is a security control, and what you see in the table is just a possible classification.
As we previously said there isn’t a standard classification nor taxonomy for security controls, for example to make things a bit more complicated (but do not worrie they are not too complicated) (ISC)2 classifies controls in 7 types based on the timing of unauthorized behaviors by motive, opportunity and means (MOM). You find them in this table:
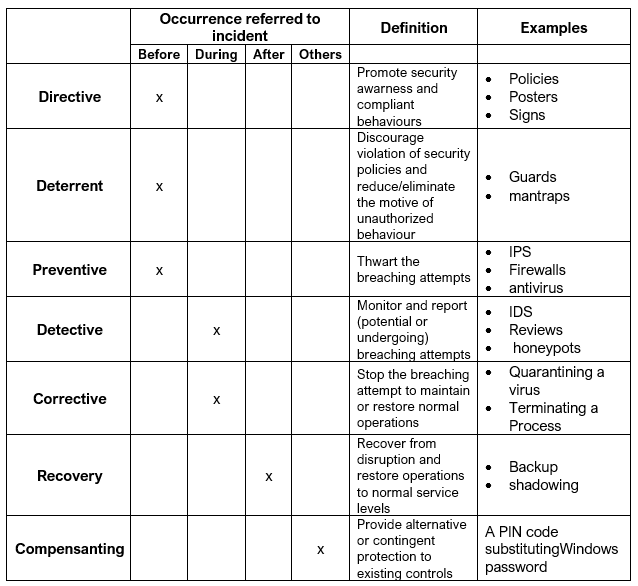
Trying to memorize any Security Control categorization, or also memorizing where a security Control is located in the table below is an exercise not useful at all. But there are some concepts that we should always take in mind when dealing with Security Controls, they are:
- The same control may fill within different classifications: Never overthink about the right classification of a control when studying for your certification or when talking to an InfoSec practitioner.
- All control types are preventive by nature.
- Preventive and Detective controls are complementary (always, when possible, first prevent and then detect)
- Implementing Security Controls must always be cost effective, it means that based on the value of the asset you are protecting the costs of implementing a security control must be less than its benefit
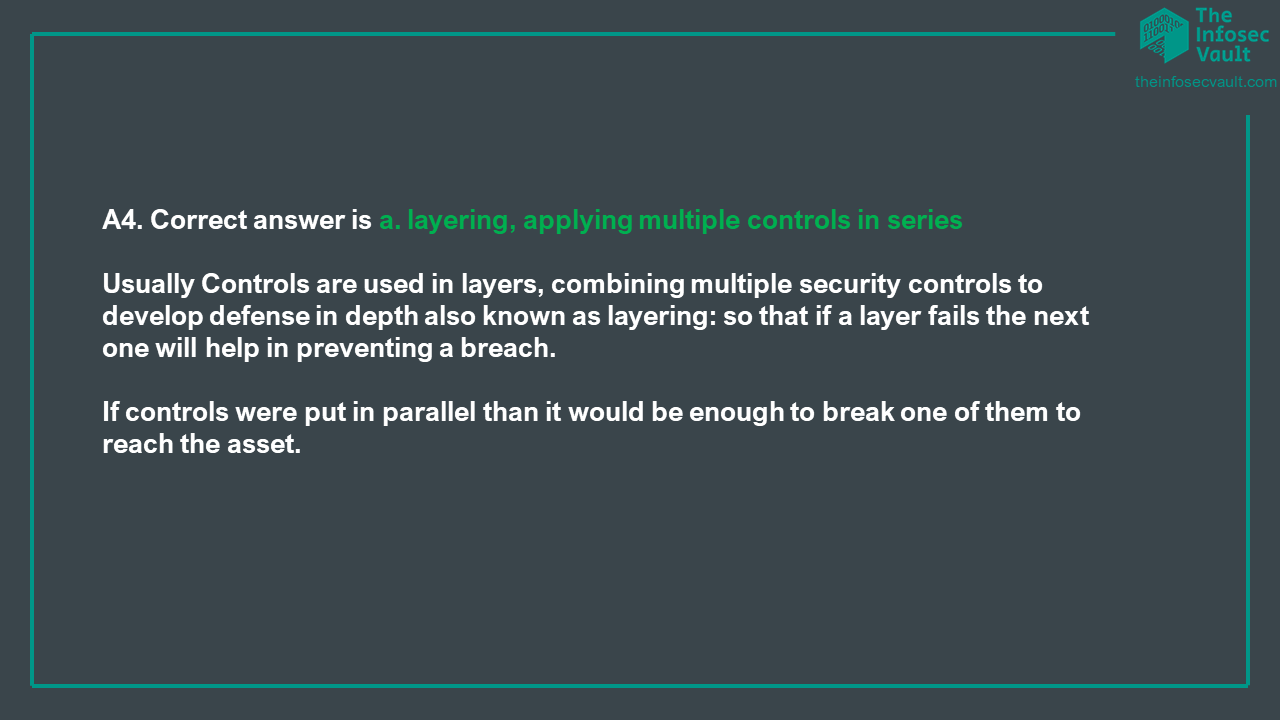
- Usually Controls are used in layers, combining multiple security controls to develop defense in depth (so that if a layer fails the next one will help in preventing a breach). To better understand this concept, you can imagine a rainbow, to reach the pot of gold you must pass through many different layers.
A Security Control Framework is a collection of security controls and implementation and audit guidelines usually organized as a template to help organizations in mitigating their risks.
Usually, Organizations select and customize security control frameworks based on their organizational needings. The selection process is also known as scoping while the customization process may be also called tailoring. Alternatively, Organizations could also build up a proprietary Security Control Framework. In the following we briefly describe 5 common Security Control Frameworks.
1. NIST Cybersecurity Framework (CSF): Developed by the National Institute of Standards and Technology (NIST), is a risk-based framework that helps organizations identify, assess, and prioritize their cybersecurity risks and implement appropriate controls to mitigate those risks. It is designed to be flexible and adaptable, and can be customized to fit the specific needs and priorities of an organization.
2. NIST SP 800-53: more detailed and prescriptive than NIST CSF,provides a comprehensive set of security and privacy controls for federal information systems and organizations. the controls were meant for agencies in order to comply with the Federal Information Processing Standards (FIPS) but many other organizations have voluntarily accepted it to assist them improve the security of their systems. It is organized into 20 control families, each of which addresses a specific area of concern, listed below:
AC Access Control
AT Awareness and Training
AU Audit and Accountability
CA Assessment, Authorization, and Monitoring
CM Configuration Management
CP Contingency Planning
IA Identification and Authentication
IR Incident Response
MA Maintenance
PE Physical and Environmental Protection
PL Planning
PM Program Management
PS Personnel Security
PT PII Processing and Transparency
RA Risk Assessment
SA System and Services Acquisition
SC System and Communications Protection
SI System and Information Integrity
Every family contains many controls (in total there are more than 1000 controls), this allows practitioners to use SP 800-53 also as a comprehensive checklist. In order to apply these controls NIST SP 800-53 prescribes a four-step process:
1. Select the appropriate security control baselines.
2. Tailor the baselines.
3. Document the security control selection process.
4. Apply the controls.
(3) ISO/IEC 27001 is an international standard that provides a framework for establishing, implementing, maintaining, and continually improving an organization's information security management system (ISMS). It includes a set of controls and guidelines for protecting sensitive information and assets, and can be used to help organizations comply with regulatory requirements and industry standards. It has 4 control categories and 93 controls. The 4 control categories are:
a. Organizational Controls
b. People Controls
c. Physical Controls
d. Technological Controls
(4) COBIT was Developed by the Information Systems Audit and Control Association (ISACA), provides a set of best practices for managing and governing information and technology (IT) assets. COBIT is not purely security focused: it deals with all aspects of information technology, security being only one component. COBIT is a set of practices that can be followed to carry out IT governance, which requires proper security practices. It includes a set of control objectives and related control practices that can be used to help organizations align their IT activities with their business objectives and mitigate risks.
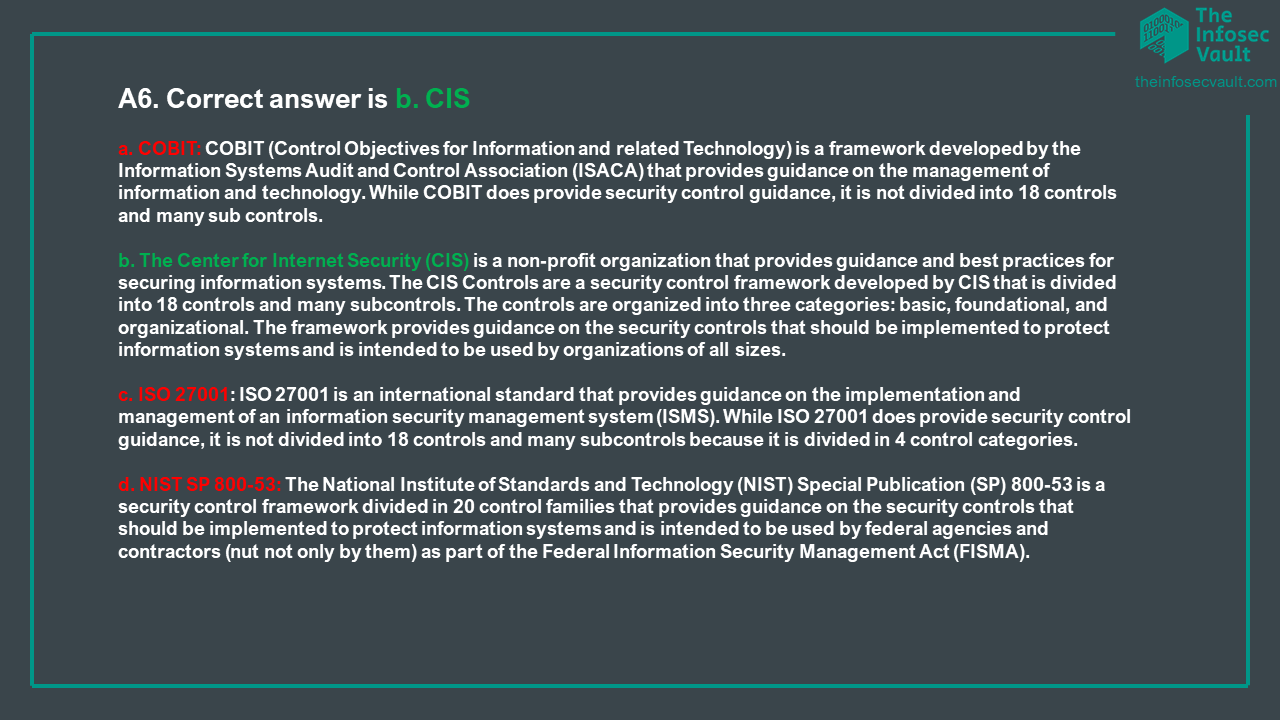
(5) The Center for Internet Security (CIS) is a nonprofit organization that, among other things, maintains a list of 18 security controls (comparable to the NIST 800-53 families )to mitigate the threat of the majority of common cyberattacks. The controls are divided in 3 families, which are:
Basic: These key controls should be implemented by every organization to achieve minimum essential security.
Foundational: These controls embody technical best practices to improve an organization’s security.
Organizational: These controls focus on people and processes to maintain and improve cybersecurity.
Under these 20 controls, CIS provides many subcontrols.
Everyone of the 5 frameworks above mentioned has its own certifications, SMEs (subject matter experts) and consultants. What was reported above was just a quick excursus to complete the topic of security controls. You can dig deeper into anyone of these frameworks with many available books or websites.
Usually, Organizations select and customize security control frameworks based on their organizational needings. The selection process is also known as scoping while the customization process may be also called tailoring. Alternatively, Organizations could also build up a proprietary Security Control Framework. In the following we briefly describe 5 common Security Control Frameworks.
1. NIST Cybersecurity Framework (CSF): Developed by the National Institute of Standards and Technology (NIST), is a risk-based framework that helps organizations identify, assess, and prioritize their cybersecurity risks and implement appropriate controls to mitigate those risks. It is designed to be flexible and adaptable, and can be customized to fit the specific needs and priorities of an organization.
2. NIST SP 800-53: more detailed and prescriptive than NIST CSF,provides a comprehensive set of security and privacy controls for federal information systems and organizations. the controls were meant for agencies in order to comply with the Federal Information Processing Standards (FIPS) but many other organizations have voluntarily accepted it to assist them improve the security of their systems. It is organized into 20 control families, each of which addresses a specific area of concern, listed below:
AC Access Control
AT Awareness and Training
AU Audit and Accountability
CA Assessment, Authorization, and Monitoring
CM Configuration Management
CP Contingency Planning
IA Identification and Authentication
IR Incident Response
MA Maintenance
PE Physical and Environmental Protection
PL Planning
PM Program Management
PS Personnel Security
PT PII Processing and Transparency
RA Risk Assessment
SA System and Services Acquisition
SC System and Communications Protection
SI System and Information Integrity
Every family contains many controls (in total there are more than 1000 controls), this allows practitioners to use SP 800-53 also as a comprehensive checklist. In order to apply these controls NIST SP 800-53 prescribes a four-step process:
1. Select the appropriate security control baselines.
2. Tailor the baselines.
3. Document the security control selection process.
4. Apply the controls.
(3) ISO/IEC 27001 is an international standard that provides a framework for establishing, implementing, maintaining, and continually improving an organization's information security management system (ISMS). It includes a set of controls and guidelines for protecting sensitive information and assets, and can be used to help organizations comply with regulatory requirements and industry standards. It has 4 control categories and 93 controls. The 4 control categories are:
a. Organizational Controls
b. People Controls
c. Physical Controls
d. Technological Controls
(4) COBIT was Developed by the Information Systems Audit and Control Association (ISACA), provides a set of best practices for managing and governing information and technology (IT) assets. COBIT is not purely security focused: it deals with all aspects of information technology, security being only one component. COBIT is a set of practices that can be followed to carry out IT governance, which requires proper security practices. It includes a set of control objectives and related control practices that can be used to help organizations align their IT activities with their business objectives and mitigate risks.
(5) The Center for Internet Security (CIS) is a nonprofit organization that, among other things, maintains a list of 18 security controls (comparable to the NIST 800-53 families )to mitigate the threat of the majority of common cyberattacks. The controls are divided in 3 families, which are:
Basic: These key controls should be implemented by every organization to achieve minimum essential security.
Foundational: These controls embody technical best practices to improve an organization’s security.
Organizational: These controls focus on people and processes to maintain and improve cybersecurity.
Under these 20 controls, CIS provides many subcontrols.
Everyone of the 5 frameworks above mentioned has its own certifications, SMEs (subject matter experts) and consultants. What was reported above was just a quick excursus to complete the topic of security controls. You can dig deeper into anyone of these frameworks with many available books or websites.
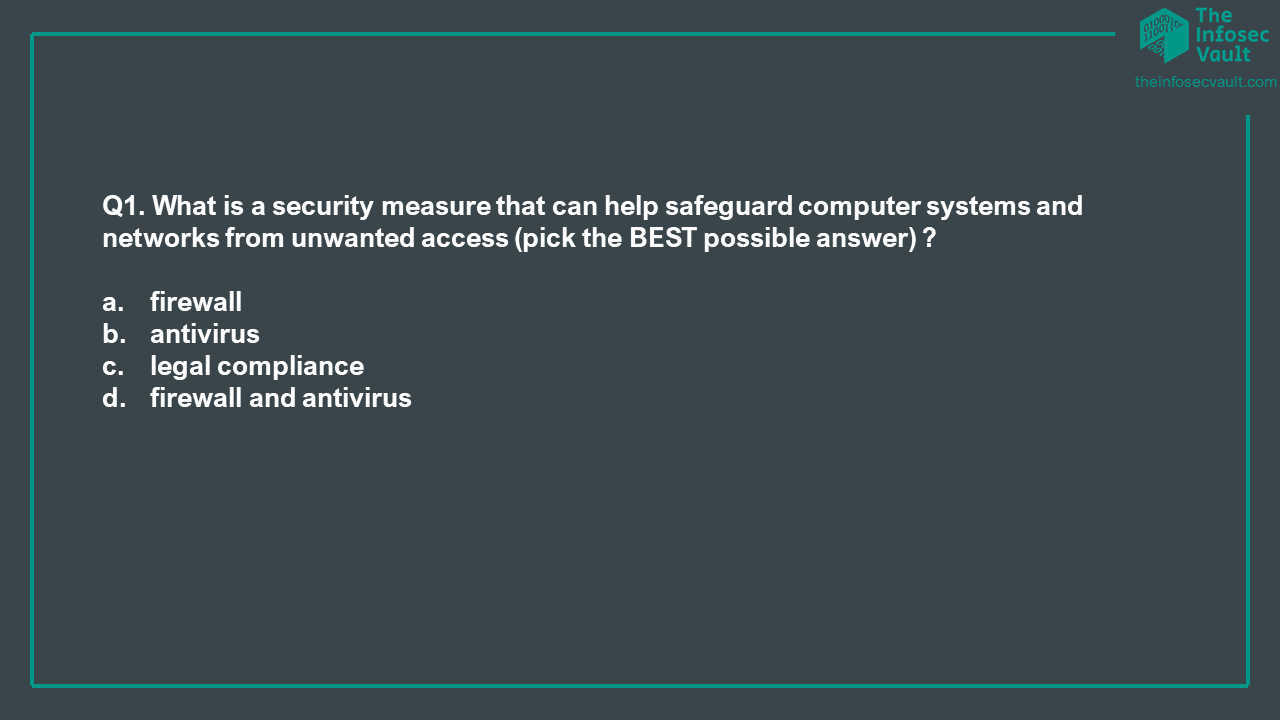
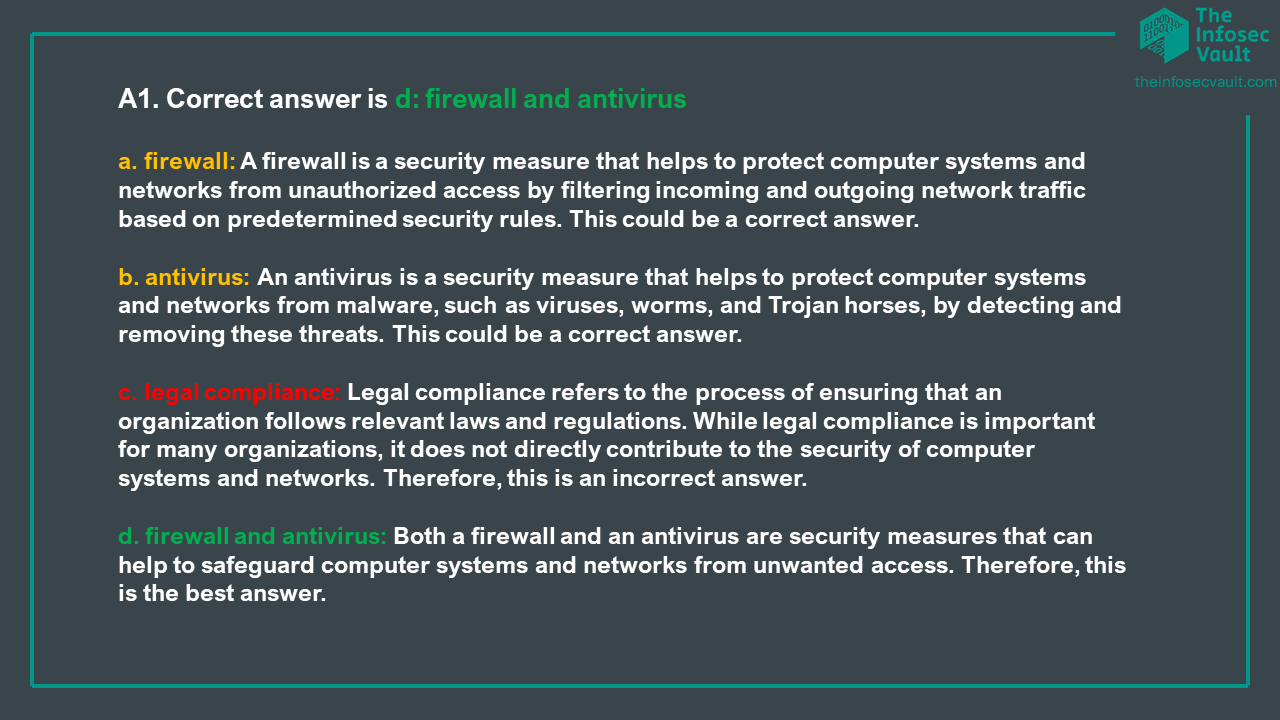
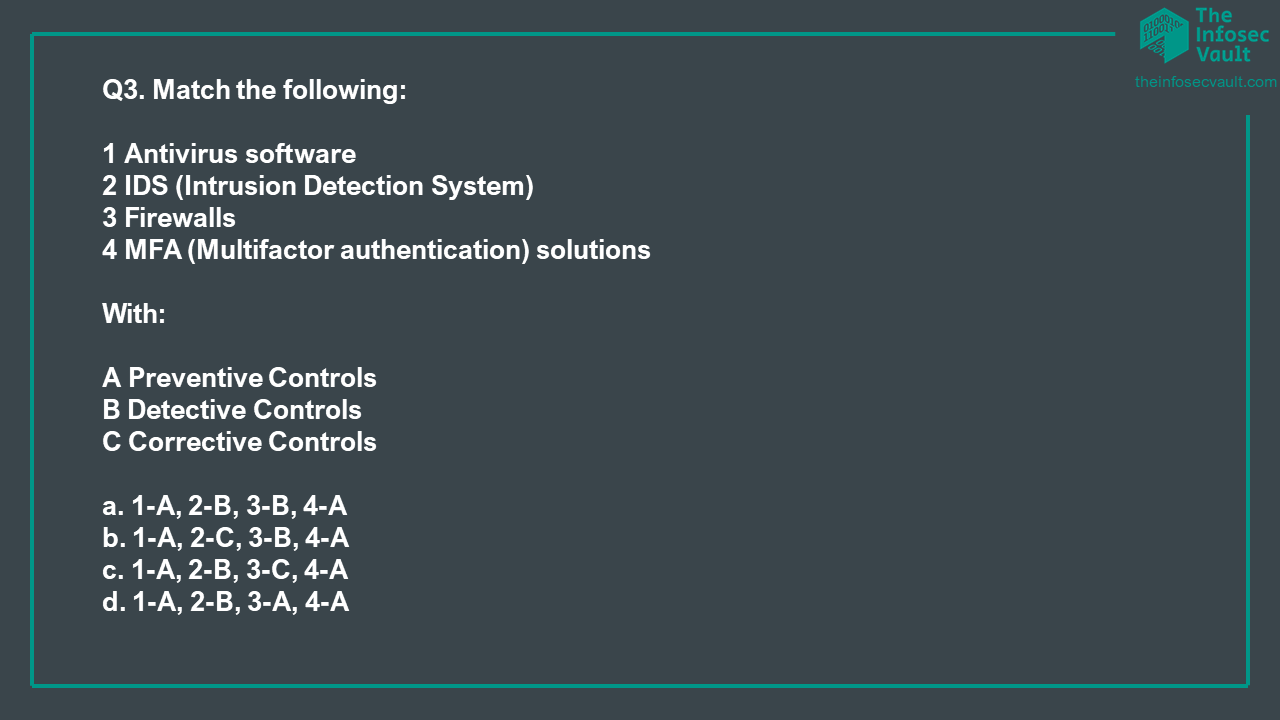
To check if you have grasped the concepts above, in the following you can find 10 multiple choice Q&A about security assets.
And finally, These are some of the terms related to Security Controls that you are supposed to remember for your certification or interview.
SECURITY CONTROL (NIST): A safeguard or countermeasure prescribed for an information system, or an organization designed to protect the confidentiality, integrity, and availability of its information and to meet a set of defined security requirements.
SECURITY CONTROL FRAMEWORK (ISC2): A notional construct outlining the organization’s approach to security, including a list of specific security processes, procedures, and solutions used by the organization.
ISMS (ISO 27000): An ISMS consists of the policies, procedures, guidelines, and associated resources and activities, collectively managed by an organization, in the pursuit of protecting its information assets. An ISMS is a systematic approach for establishing, implementing, operating, monitoring, reviewing, maintaining and improving an organization’s information security to achieve business objectives. It is based on a risk assessment and the organization’s risk acceptance levels designed to effectively treat and manage risks.
VERIFICATION: Verification is the process of evaluating a product, process, or system during or at the end of the development process to determine whether it satisfies the specified requirements. (In the context of security control, verification is used to verify if a control satisfies the requirements). Verification activities typically involve reviews, inspections, and other activities that are designed to ensure that the product or system is designed and implemented correctly. Verification answer the question “did we build the product right?”
VALIDATION (many sources): The act of performing tests and evaluations to test a system’s security level to see if it complies with security specifications and requirements. Is an important quality assurance activity used (often together with verification) in the development of products, processes, and systems. Validation activities are focused on determining whether a product or system performs as intended when used under specified conditions. Validation answer the question “did we build the right product ?”
DEFENSE IN DEPTH (NIST SP 800-53): An information security strategy that integrates people, technology, and operations capabilities to establish variable barriers across multiple layers and missions of the organization.
INCIDENT (FIPS 200): An occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.